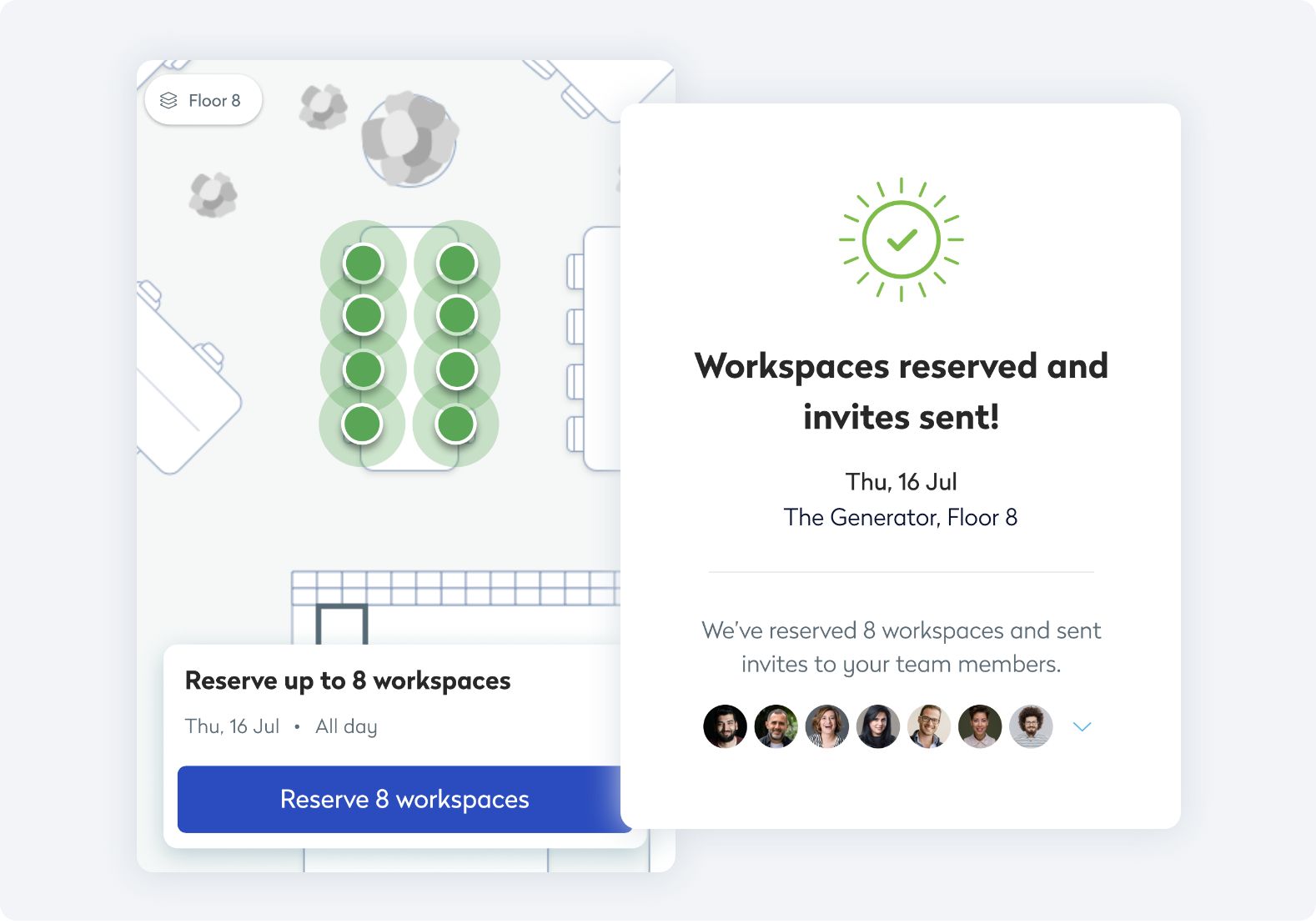
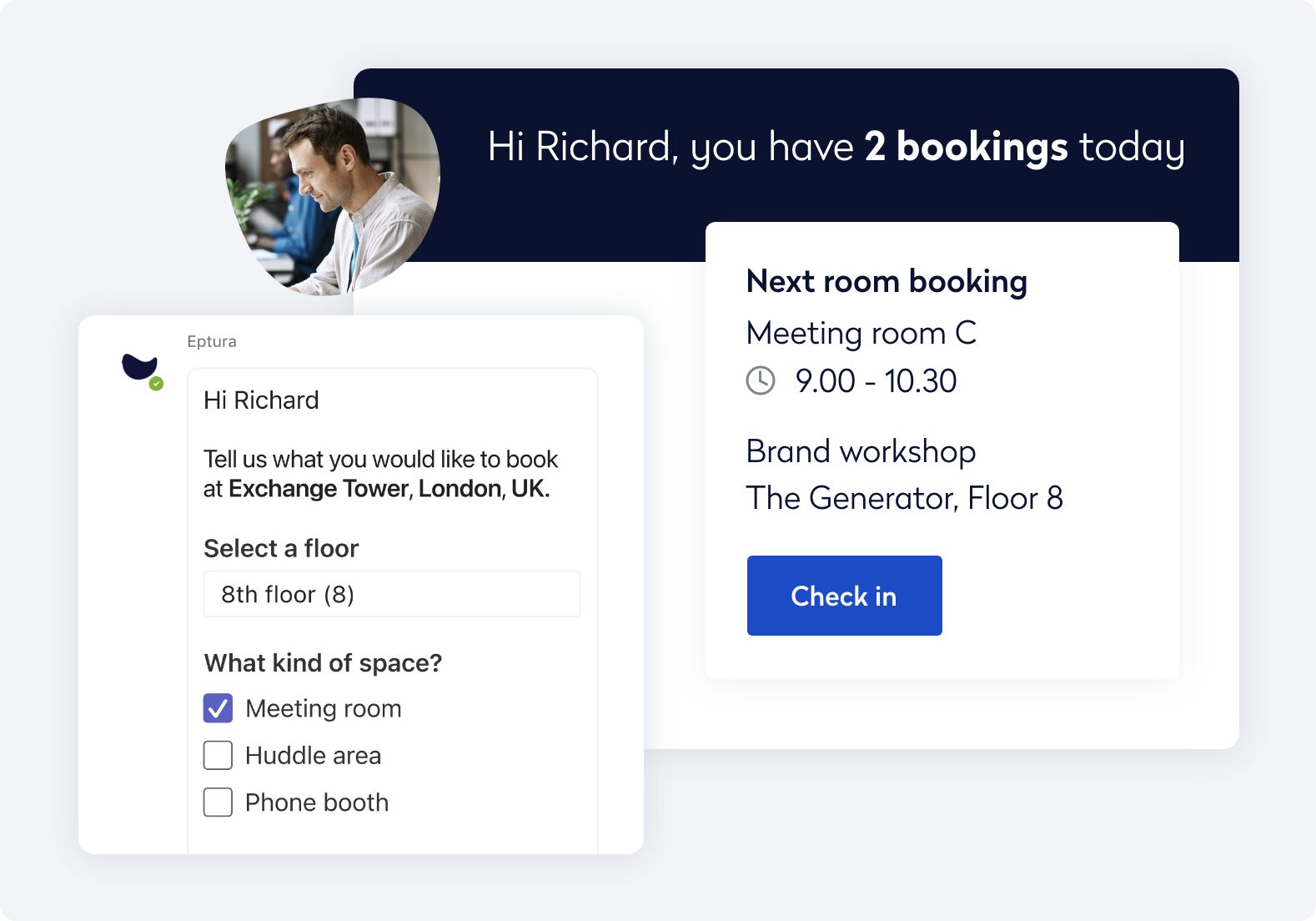
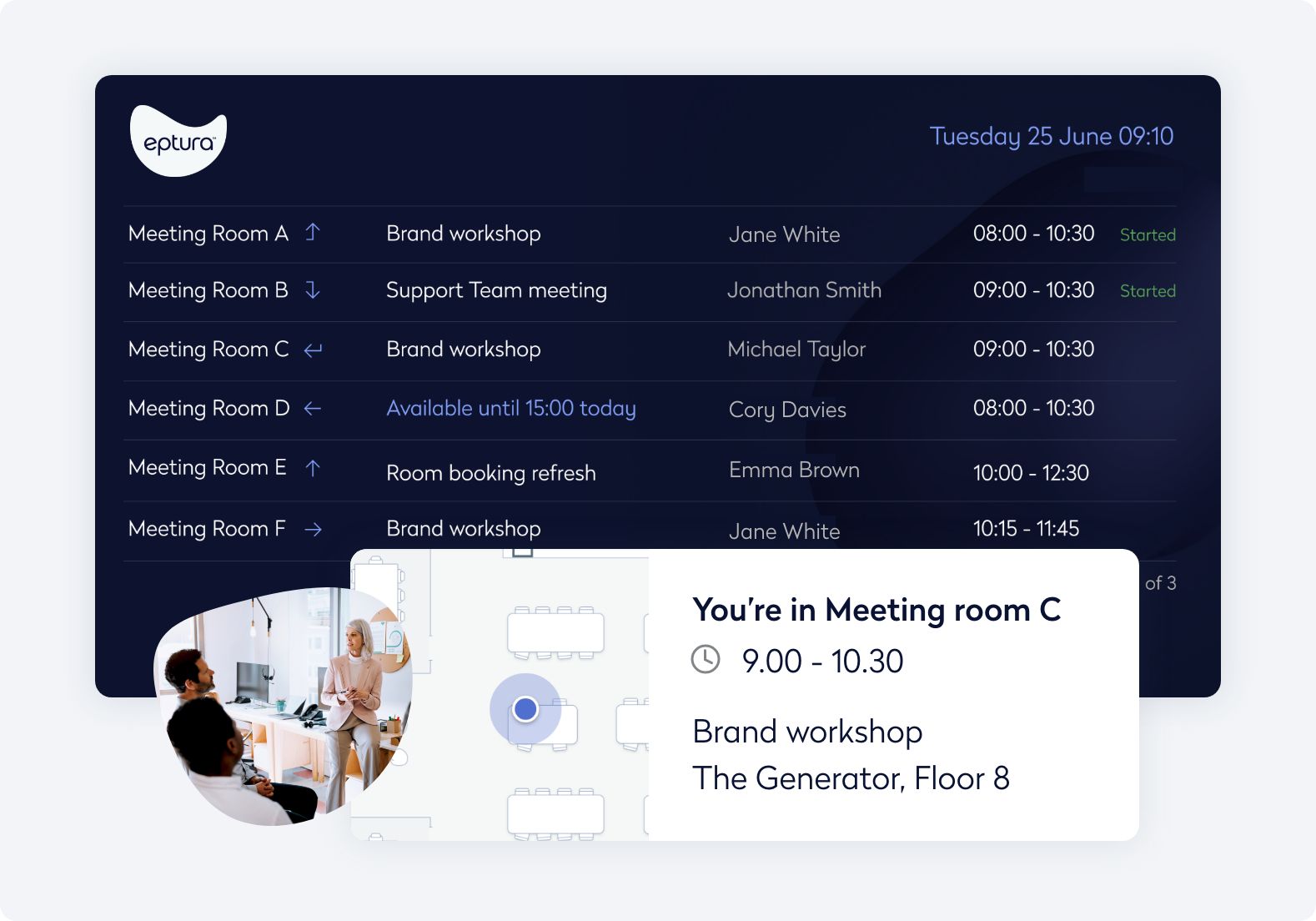
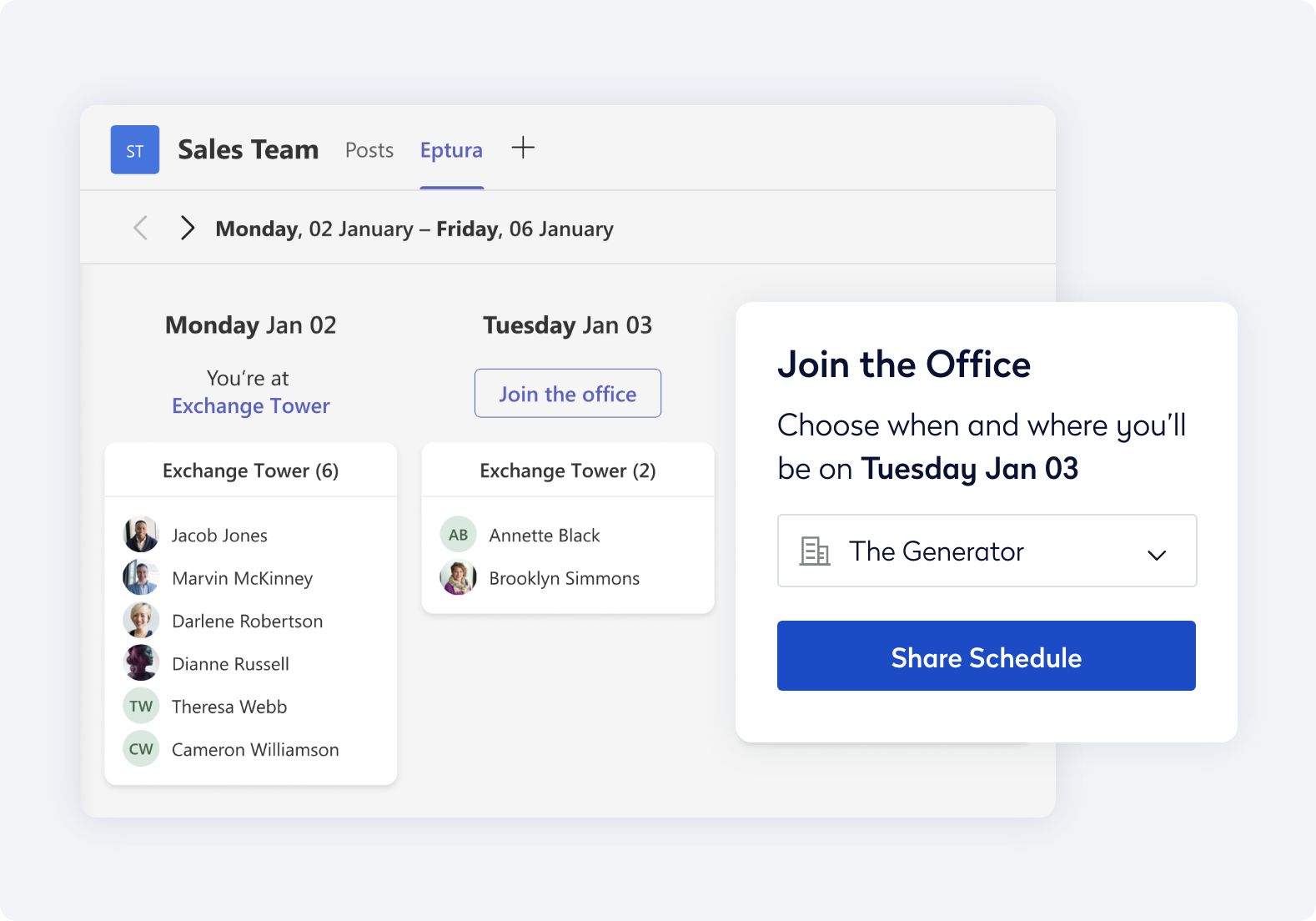
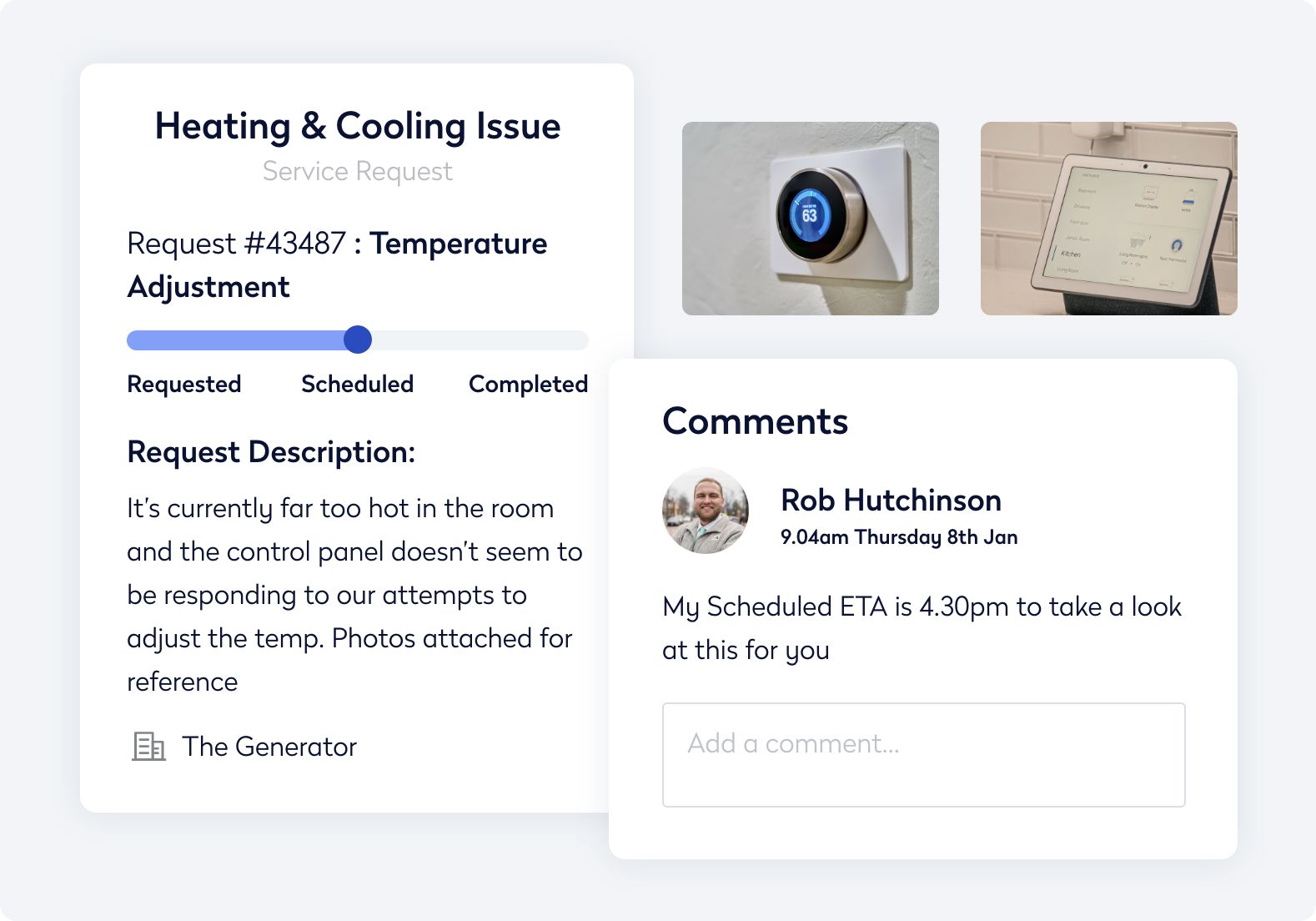
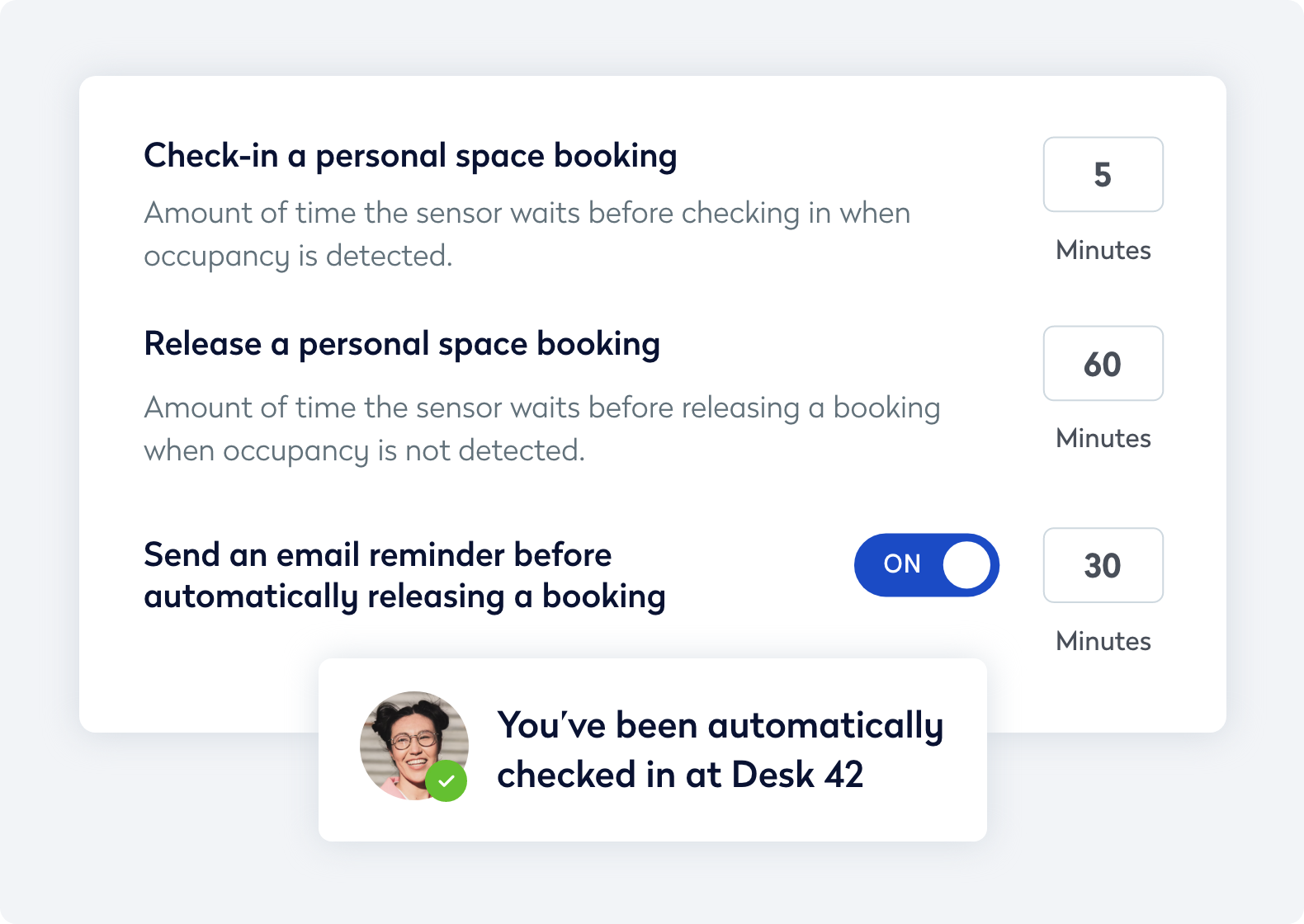
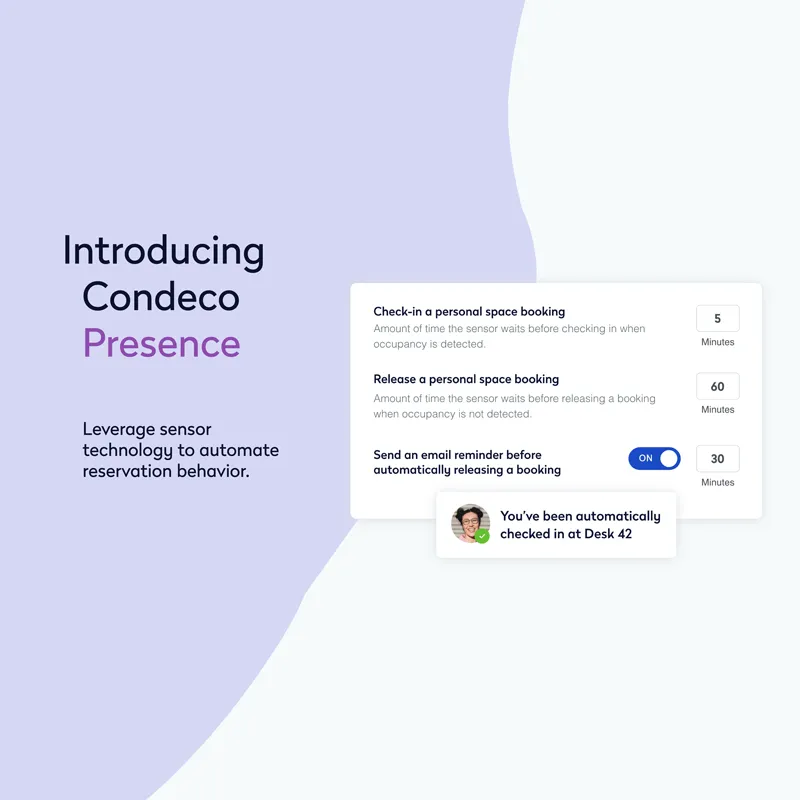
Simplify wayfinding and manage service requests directly in the Eptura mobile app.
- What we do
-
Our platform
With Eptura’s all-in-one platform, you can bring together your entire world of work, so your people — and your business — can reach their full potential
- Product portfolio
- Services
-
Our platform
- Industries
- Who we partner with
-
Resellers
Partnering with the best local experts to meet your needs
-
Autodesk Alliance
Building future-proofed workplaces ready for tomorrow
-
Corporate real estate
Transforming space utilization for the future of work
-
Tech partners
Integrating seamlessly with the tools you use every day
-
Become a partner
Collaborating to create a better world of work for everyone
-
Resellers
- Our Plans
- Discover more
-
Resources
Access a wealth of expert resources for yourself, your team, and your organization.
-
Blog
Read insightful articles filled with can’t-miss tips and research
-
Podcasts
Listen to thought-provoking conversations with industry experts
-
News
Catch up on all the latest from Eptura HQ
-
Events
Browse our upcoming live and virtual events
-
Resources
- About us
-
Our vision
See how we’re building a future where everyone can thrive
-
Our values
Discover what motivates our work
-
Our impact
Learn how we support workplace equality and the planet
-
Our team
Get to know the people behind our mission
-
Our offices
Find us in locations around the world
-
Careers
Join our growing team of innovators
-
Our vision